Zyston Client Program Managers Provide An Elite Standard Of Service That Sets Zyston Apart From Other MSSPs
Much like the cyber threat environment, Zyston is evolving, continually striving to meet the needs of today’s business environment.
We’ve recently expanded, adding critical new talent to our team; plus, we’re rolling out an exciting new feature that improves interactions between the client’s security team and the Zyston system. Our new Client Program Manager feature delivers a more customized, tailored approach to your needs, creating a compelling differentiator vs. competing MSSPs.
Zyston Client Program Manager
Our Client Program Managers (CPM) represents an elite standard of service among MSSPs. Each client is assigned a dedicated CPM to serve as an onsite or virtual point of contact, bridging the communication gap between a client’s information Security Group and the Zyston Security Operations Center. In essence, it’s a way for us to answer your needs more precisely and tailor our service to individual concerns and risk levels. In addition, a Zyston CPM is also responsible for reviewing security incidents, conducting a root cause analysis (RCA) and then ensuring that all security incidents are fully remediated. Other MSSPs simply send over alerts and leave it to your internal IT team to diagnose and remediate. Zyston isn’t like other MSSPs and with our Client Program Manager team we have the ability to go beyond the alert.
Ultimately, having a dedicated CPM is an extra layer of protection, ensuring no opportunities are overlooked and all incidents are fully diagnosed and remediated in order to keep your organization and its vital data secure.
We Start With The CyberCast Security Assessment
Zyston’s CyberCast Security Assessment delivers critical insights into your threat susceptibility. Through a combination of technical penetration testing and a detailed security assessment, CyberCast scores your security risk and compares your vulnerability against industry standards. Based on these results, we then establish an action plan to improve your score systematically.
Once your CyberCast is complete, the CPM leverages the intelligence contained in the report to prioritize and coordinate tactical reduction of organizational security risks.
We know that cybersecurity is never a “one-size-fits-all” solution. And while it might be tempting for your security team to go with an off-the-shelf solution, a more detailed approach will yield better results. Suffice to say, the less you have to focus on cybersecurity, the more time you’ll have to devote to other things. Zyston with CPM takes those worries off your plate, giving you and your IT team back their valuable time.
How Zyston With CPM Works
The Client Program Manager maintains regular contact with a client’s IT/Security teams in an effort to fully understand their security needs and expectations. Combining high-level cybersecurity expertise, business intelligence, and customer support at its best, they provide valuable feedback on a regular basis to ensure complete cybersecurity coverage and alignment across people, process, and technology, according to customer demands.
Zyston CPMs attend meetings, update upper managers on the status of important security findings, conduct root cause analyses (RCA’s) and closely collaborate with key employees to identify the best possible course of action as well as ensure full remediation of all incidents. It’s like having an extension of your IT team without the extra expense, as the service is built into the Zyston solution.
Filling The Gaps
In typical outsourced or managed services scenarios, there are often gaps that go unfilled because either the provider is not specifically connected to the customer or the customer doesn’t know the gap exists. If this was merely a customer service scenario, these shortfalls might amount to little more than an inconvenience, but since we’re talking about cybersecurity, there’s a lot more at stake. A simple oversight can multiply quickly in a threat environment, leading to data loss and impacting business continuity and reputation.
So, while your current MSSP system might offer better protection than you would have without, a little more attention to detail will improve its efficacy massively. In that sense, the value of having a single point of contact can’t be understated. Your CPM is 100% committed to ensuring your organization’s protection—you might think of them as your own personal protector, a trusted advisor who is (arguably) just as passionate about your success as you are.
Zyston Ranch Access
We realize that top-level cybersecurity is an ongoing process and that improvements don’t happen in a vacuum. As a result, all Zyston CPMs have access to the Zyston Ranch, a combination of the Security Operations Center (SOC) and the Advisory Group, providing them with unprecedented access to expert guidance and advice on how best to execute the role and responsibility of their position.
The CPM leverages insights gained from the Zyston SOC and translates them back to the customer in ways they can understand. In essence, they act as the point person between highly technical security operations and your on-premise team to ensure success.
CPM Success In Action
We have witnessed, first-hand, the positive impact that Client Program Managers have in supporting our customers’ cybersecurity needs. Based on these metrics, we decided to include this function in all of our cybersecurity service offerings. In the effort to improve customer success in an area that hinges on fast response and agility, a dedicated CPM offers complete peace of mind as you’ll know that every possible scenario has been considered.
Not to throw shade on our competitors, but we now stand in strong contrast to other MSSPs who do not engage at this level and communicate solely through online ticket systems. By utilizing a CPM, Zyston’s clients have, without exception, experienced very smooth and seamless onboarding—which is a markedly different experience from current industry standards.
All this is to say, Zyston is and has always been 100% committed to customer success. At our core, we are solutions providers and problem-solvers, so we would be remiss in thinking that there is no room to improve.
In the constant effort to provide superior value for our customers, we recognized shortfalls in the current MSSP space. We feel that these are problems that can’t be solved by throwing technology or automation at them. In order to create a more agile, malleable, and bespoke approach to service delivery, we applied our best resource to it, and that’s our people.
Which leads us into the next bit of business…
Our Team is Growing!
Zyston continues to make investments into growing our value proposition. To support these efforts, we’ve recently added numerous new employees to our team, many of whom have proudly served our country with distinguished military experience.
Client Program Manager
Amber Williams
Amber Williams has eight years of experience and training in managing infrastructures and security programs across multiple platforms. Her knowledge of security began with the US Navy. After four years of honorable service, she joined the civilian sector, first as a Linux SysAdmin. She soon discovered a passion for Information Security during an incident response exercise. She prides herself in the growth she’s facilitated, not only with each company she’s worked for but also personally and professionally.
Client Program Manager
David Day
David Day is a Certified Information Systems Security Professional (CISSP), with expertise in the design, implementation, and management of network infrastructure and security and a proven record of evaluating system vulnerabilities and recommending security solutions aligned with business processes and objectives. David is adept at critical and strategic thinking that leads to innovative solutions to complex problems involving various information systems. Self-motivated and disciplined, he is able to work independently or collaboratively on large-scale projects while directing multiple programs from concept to implementation. He offers a strong sense of responsibility and accountability with an approachable leadership style that promotes a culture of high-performance and results, leveraging 30 years of experience in the IT and InfoSec fields in both the military (27 years) and private sectors. Throughout his career, he has led IT and InfoSec teams from as small as a few to as many as 100+ in some of the roughest conditions, both stateside and deployed in combat zones.
Client Program Manager
Michael Randazzo
Michael Randazzo has over 18 years of Information Technology experience in various areas of Security, Compliance, and System/Network Administration, Michael’s broad range of expertise gives him the ability to fulfill various roles within Information Technology. Michael’s unique background in Security and Governance & Risk Management has enabled him to design, implement, and support security solutions in alignment with business strategies and objectives. By taking personal responsibility for managing and architecting projects with enterprise strategies and focus, he exhibits leadership and commitment to achieving business objectives.
Client Program Manager
Stewart Wolfe
Stewart Wolfe is originally from South Carolina and graduated from the University of Coastal Carolina in 2008 with a Bachelor of Science in Business Administration Marketing. He joined the Air Force in 2009 and served four years active duty with two deployment tours as an Airmen Client System Technician. He then transitioned to the Air Force Reserved as a Cyber Warfare Defense Operator while working as a Desktop Support Supervisor/Manager for First Financial Bank. In 2014, he was hired by FinTech company Oportun as a Cyber Security Engineer. In 2018, he transitioned Air Force reserved units to serve as a Noncommissioned Officer in Charge of the Communications Focal Point at Naval Air Station Joint Reserve Base Fort Worth and was promoted to Cyber Security Staff Engineer with Oportun. In February 2021, he joined Zyston as a Cyber Security Architect/Client Program Manager while proudly continuing to serve in the Air Force Reserve. Stewart’s Certifications include EC-Council Certified Ethical Hacker, CompTia A+, CompTia Security +, Comptia Advanced Security Practitioner (CASP+), and MCSA Windows 10. He completed Sumo Logic Certifications for Fundamentals, Search Mastery, Administration, and Security.
Client Program Manager
Travis Pille
Travis’ strong suits are SIEM analysis and threat hunting, EDR, and incident response with strong proficiencies in ServiceNow reporting and dashboards. He also has hands-on experience with Proofpoint (TAP and TRAP), O365, Azure AD, SOAR (Demisto), and scripting (PowerShell, Python, VisualBasic, etc.). Accomplishments from previous jobs include developing an Incident Response plan for a major international airport, and engineering and demonstrating a threat simulation lab for demonstrating detection and response tools (SIEM, network UEBA, SOAR). At Zyston, Travis’ successes include optimization of NCL reporting to reduce the workload of weekly metrics reports by 50%, performing best practice assessments for CrowdStrike and O365, developing an account compromise remediation plan, and assisting is resolving multiple major security incidents. His certifications include GCIH (GIAC Certified Incident Handler), GISP (GIAC Information Security Practitioner), CISSP (exam passed, endorsement process in progress).
Client Program Manager
Conner Lunsford
Conner acts as the Program Manager within Zyston’s Security Operations Center (SOC) and interacts closely with the Advisory practice. He has equal experience conducting strategy assessments and design workshops as he does executing tactical implementations and managing client deliverables. Conner’s expertise covers a wide range of industries and capabilities including Consumer Products, Manufacturing, and Healthcare as well as Systems Implementation and Strategy Development. Prior to joining Zyston, Conner worked as a technology consultant at a big four consulting firm, operating as an implementation and design lead for SAP offerings.
Client Program Manager
Phil Den Hoed
Phil Den Hoed is an accomplished IT professional with more than 15 years of hand-on experience working with a diverse array of technologies, Phil thrives on the challenge of analyzing, investigating and providing effective infrastructure solutions. Phil boasts numerous cybersecurity certifications and is also a Microsoft Certified Systems Engineer.
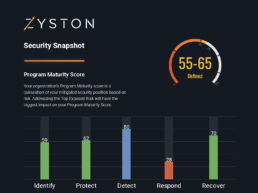
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.





























