In the evolving landscape of cybersecurity, one truth stands clear: threats are relentless. Cyber adversaries are continuously adapting, devising new methods to bypass defenses, exploit vulnerabilities, and compromise organizations’ most valuable assets. To counteract these dynamic threats, a revolutionary approach to cybersecurity is emerging—Continuous Threat Exposure Management (CTEM). As businesses seek to safeguard their operations in this era of persistent cyber risk, CTEM represents a paradigm shift, offering a comprehensive strategy that integrates proactive threat detection, rapid response, and ongoing resilience against attacks.
The Evolution from Traditional Security to CTEM
For decades, organizations have relied on a variety of security measures—firewalls, intrusion detection systems, and antivirus software—to protect their digital ecosystems. However, these traditional defenses, while effective against known threats, often fall short in detecting and responding to sophisticated, novel attacks. The rise of advanced persistent threats (APTs), zero-day exploits, and increasingly sophisticated social engineering tactics has exposed the limitations of static security postures. In response, the cybersecurity industry has recognized the need for a more dynamic and continuous approach—one that doesn’t merely react to threats but anticipates, mitigates, and adapts to them in real time.
Continuous Threat Exposure Management (CTEM) is the answer to this challenge. It represents a strategic shift from reactive to proactive cybersecurity, emphasizing the need for continuous visibility into the threat landscape and the ability to respond swiftly to emerging risks. CTEM is not a single product or tool but a holistic approach that integrates various technologies, processes, and best practices into a unified framework. This approach enables organizations to manage their cyber risk exposure continually, adapting to the changing threat environment and ensuring that security measures are always one step ahead of potential attackers.
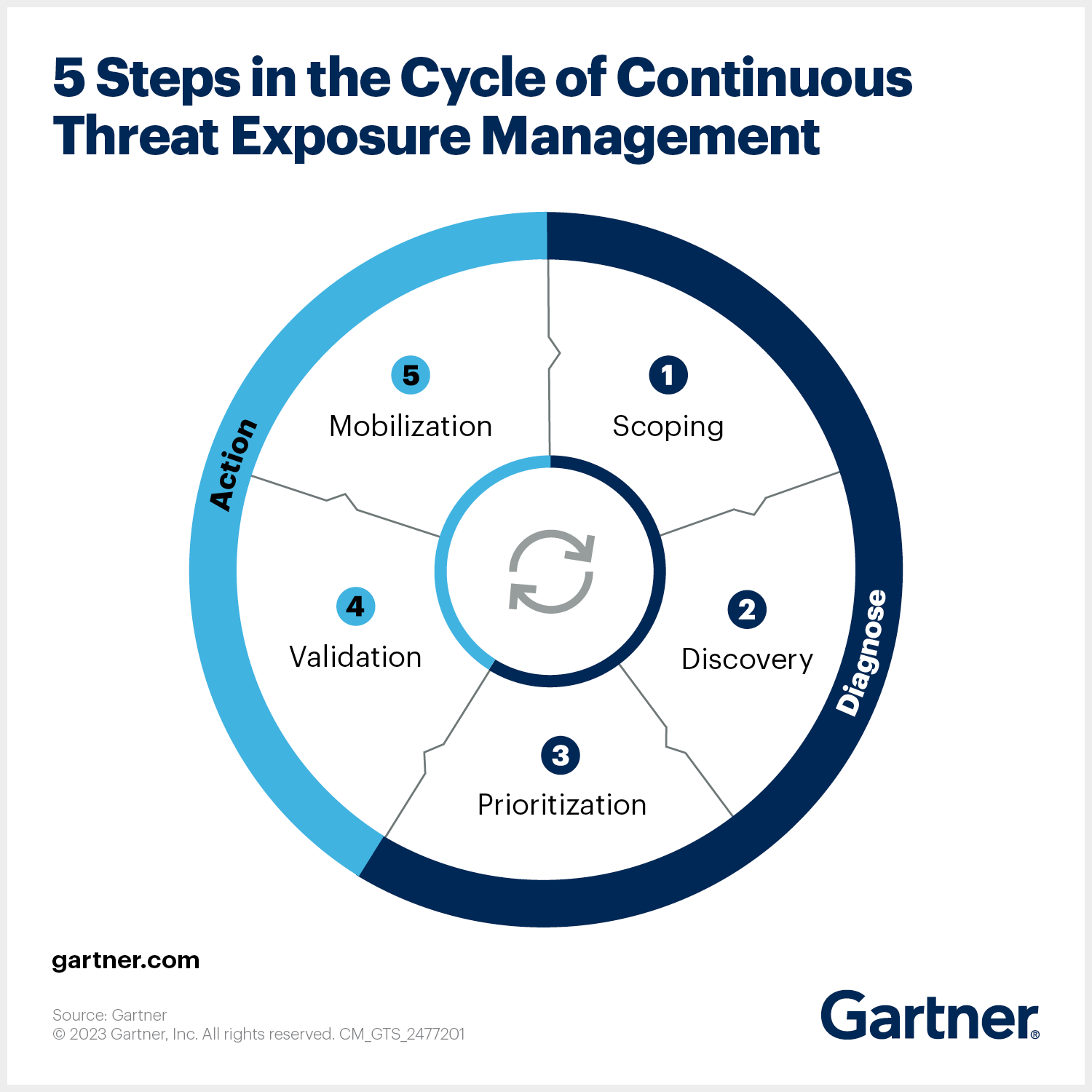
Key Components of CTEM
To fully appreciate the value of CTEM, it’s essential to understand its key components, which together form a comprehensive defense strategy:
- Continuous Monitoring and Threat Intelligence: At the core of CTEM is the ability to monitor an organization’s environment continuously. This involves leveraging advanced threat intelligence tools to gather real-time data on potential threats. By continuously analyzing this data, organizations can detect anomalies, identify patterns indicative of an attack, and assess the potential impact of these threats on their operations.
- Proactive Risk Management: Traditional risk management often relies on periodic assessments, which can leave organizations vulnerable during the gaps between evaluations. CTEM, however, adopts a proactive stance, where risk management is an ongoing process. This involves regular updates to threat models, continuous vulnerability assessments, and real-time prioritization of risk mitigation efforts based on the latest intelligence.
- Continuous and Intelligent Validation. Findings are key, but the signal to noise ratios are often misaligned and lack actual relevancy. Validating findings for prioritization and eventual remediation drive intelligence for the overall CTEM cycle and become a critical path for successful implementation.
- Automated Response and Remediation: Speed is of the essence when it comes to cybersecurity. The longer a threat goes unaddressed, the greater the potential damage. CTEM emphasizes automation in threat response, enabling organizations to deploy countermeasures rapidly and effectively. Automated systems can isolate infected segments of a network, patch vulnerabilities, and even neutralize threats without human intervention, significantly reducing response times and limiting damage.
- Resilience and Recovery Planning: While preventing attacks is the goal, preparing for the worst is a necessity. CTEM includes robust resilience and recovery strategies, ensuring that organizations can bounce back quickly from any security incident. This includes automated backup systems, disaster recovery planning, and regular testing of recovery processes to ensure they function seamlessly in the event of an attack.
- Continuous Improvement and Adaptation: The threat landscape is not static; it’s continually evolving. Therefore, a successful CTEM strategy must include a commitment to continuous improvement. This involves regularly updating security protocols, incorporating lessons learned from past incidents, and staying abreast of emerging threats and technologies. By fostering a culture of continuous learning and adaptation, organizations can ensure that their security measures remain effective over time.
CTEM in Practice: Empowering Leading Solutions
For organizations to fully realize the benefits of CTEM, they need access to cutting-edge tools and platforms that support this continuous, adaptive approach. Leading cybersecurity solutions that embody the principles of CTEM offer a range of features designed to provide comprehensive protection.
One such solution could be CyberCAST, a market leader in CTEM, which exemplifies the integration of these key components into a seamless platform. CyberCAST offers continuous monitoring through its advanced threat intelligence capabilities, providing organizations with real-time visibility into their security posture. Its automated response features ensure that threats are addressed swiftly and effectively, minimizing the potential impact of attacks. Moreover, CyberCAST is built with scalability and adaptability in mind, allowing organizations to customize their security strategies based on specific needs and evolving threats.
By utilizing CyberCAST organizations can transition from a reactive security posture to a proactive, continuous defense strategy. This transition not only enhances their ability to prevent and mitigate attacks but also instills confidence that they are equipped to handle the complex, evolving nature of modern cyber threats.
The Future of Cybersecurity: Embracing CTEM
As cyber threats continue to grow in complexity and frequency, the need for a continuous, adaptive approach to cybersecurity becomes increasingly clear. CTEM represents the future of cyber defense, offering organizations a comprehensive framework that not only addresses current risks but also anticipates and prepares for future challenges.
For cybersecurity leaders, adopting CTEM is not just a strategic choice—it’s an imperative. By embracing CTEM, organizations can position themselves at the forefront of cybersecurity innovation, ensuring that they are not only defending against today’s threats but also preparing for the unknown challenges of tomorrow. In this rapidly changing landscape, the organizations that thrive will be those that are continuously vigilant, relentlessly adaptive, and fully committed to protecting their digital assets in an ever-evolving threat environment.
The journey to CTEM is one of continuous improvement, resilience, and foresight. For those leading the charge, it’s a journey worth embarking on—because in cybersecurity, standing still is not an option.
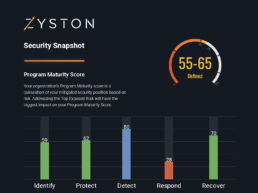
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.





















