CVE-2022-30190 – Microsoft Support Diagnostic Tool (MSDT) / “Follina” RCE VulnerabilitySummary: A zero-day remote code execution (RCE) vulnerability has been identified in the Microsoft Support Diagnostic Tool (MSDT). The vulnerability is being actively exploited by multiple threat actor groups including at least one Chinese advanced persistent threat (APT) group according to Proofpoint. At this time, no patch has been released by Microsoft, but the recommended mitigation by Microsoft is disabling the MSDT URL protocol (more details below). We would recommend testing the mitigation before deploying it to a production environment. It’s recommended to patch as soon as possible once it’s released. Additionally, endpoint detection and response (EDR) solutions have options such as “Suspicious Process Blocking” by CrowdStrike and an attack surface reduction (ASR) rule “BlockOfficeCreateProcessRule” for Microsoft Defender for Endpoint that will aid in detecting and/or preventing successful exploitation. |
 |
Protecting ExecutivesSummary: The rise of data brokers has allowed people’s personal information to be easily accessible over the internet. A concerning trend of targeting executives has also been on the rise. A recent study shows that 99% of executives can be found in more than three dozen data broker websites. Using information gathered from data brokers has allowed cybercriminals to physically threaten executives. Why it matters: Personal information of citizens should always be protected, even more so for executives of companies who hold power over decision making. By allowing personal information to be publicly available, data brokers have made it easier for malicious actors to bridge the gap between the cyber and the physical. With the increasing political tension in today’s climate, criminals have been more emboldened in attacking people with opposite viewpoints. Executives who made certain cultural and political stances have been targets of physical threats. These threats have become more common today given the ease of access to executives’ personal information through data brokers. Thus, the best action to ensure the safety of executives would be to have them opt out of data brokers’ systems. |
Insider Risks in a Hybrid-Remote Work EnvironmentSummary: The pandemic-led workplace change has allowed many employees to work from home permanently or on a hybrid basis. The acceleration was assisted by the use of cloud technology which allowed users to access files remotely without the limitation of physical location. While the benefits of cloud technology have made it easier for companies to lessen the burden of location constraints, the technology is not without its vulnerabilities. Companies that have engaged in the transition to a cloud-based workforce are now at an increased risk of sensitive data exfiltration via Cloud. This transition has also coincided with an increased concern of insider threats in recent years. Why it matters: Sensitive data is data that can have a wide range of effects to individuals as well as companies. This type of data is usually protected via regulations through both physical and cloud-based storage. The concern comes in the form of the ease of access employees can access this type of information. While the implementation of cloud environments has been beneficial for employees to connect remotely; security teams commonly do not have the same level of visibility to the hosts. This concern can stem from the malicious or accidental actions of an insider individual. Such actions can have a significant impact on the affected parties. |
 |
 |
Phishing Attacks Continue to Trend UpwardsSummary: Over the month of May, phishing continues to be a common trend in both news outlets and in the Zyston SOC’s day-to-day alerts. Higher-effort phishing attempts tend to trend towards either using personally identifiable information such as a name or a company/service name or disguising itself with current events such as this article in which Ukrainian refugees are warned of a chemical attack and tricks users into interacting with macro-enabled Excel documents that load and spread malware. Why it matters: Phishing is and continues to be one of the top issues facing individuals across the board and is always one of the most common security threats to occur. This article by Clario states that Phishing is up 510% from January to February 2022 and is costing companies significant amounts of money. Therefore, security professionals will always make efforts to educate users on the importance of security awareness. We’ve attached some resources below to help educate employees on the importance of phishing awareness and readiness to combat the ever-growing threat of these attacks. Here are a couple of the most relevant tips from Proofpoint: Tip 1: Don’t trust the display name |
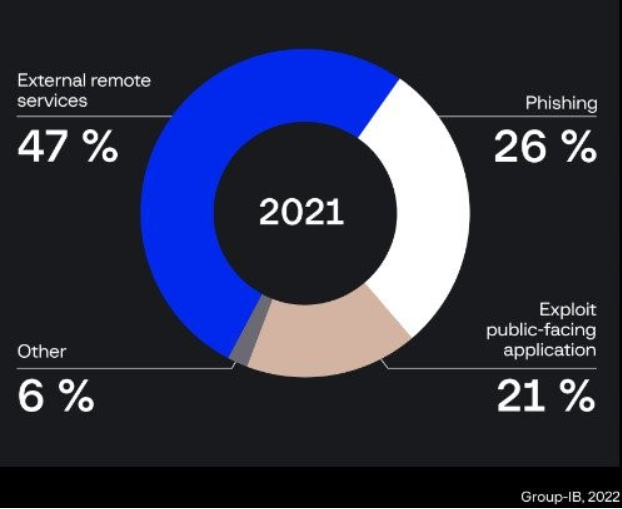
Ransomware Updates in MaySummary: Based on this BleepingComputer article, ransomware appears to have slowed down in the latter half of May. However, ransomware continues to hit groups such as Chicago public schools and Costa Rica declaring a national emergency due to ransomware attacks by Conti. In the case of Conti, it appears that recent intel has indicated the gang is publicly “slowing down activity” but not halting operations and will be splitting into “cells” that can aid them in avoiding detection. Security researchers are warning that recent ransomware attacks appear to be trending towards exploiting existing vulnerabilities such as exposed RDP servers. A joint report by experts in the field indicates the number of vulnerabilities that are associated with ransomware have grown to 310 in the first quarter of 2022. The following image displays the current breakdown on primary methods of compromise by ransomware: Why it matters: While it is true that ransomware has slowed down in recent months, it continues to be one of the costliest and most interesting trends in the Security space. It is always recommended to stay up-to-date and protected against up-and-coming attacks. |
 |
 |
Security Tip of the MonthSummary: For this month, we’d like to continue to emphasize the importance of data hygiene for security teams. Companies are discovering that their security teams must understand security threats and be proactive about fixing and remediating quickly to prevent or lower the impact of attacks. Here are some best practices we’d recommend from this blog by LoginRadius and this blog by TechTarget as a short checklist:
|








