Adversarial Offensive Security is an assessment aiming to provide a highly accurate view of the risk technology poses to a business and to ensure that business outputs are secure enough to be released or in production. These assessments mimic an attack as closely as possible to audit business readiness, blue team defences, and cybersecurity ideals, such as in-depth-defense.
Only a select number of people in the business are aware of the Adversarial Exercises being performed. This ensures the reactions and defenses are as close to the real-world as possible.
Traditional Penetration Testing
Penetration Testing focuses on a specific area at a time, such as the external or internal network, a web or mobile application, or a sub-section of each. The value is that the developers, system administrators and security engineers can validate their security efforts and ensure that any vulnerabilities or misconfigurations are caught.
Conducting penetration tests is a critical step in the software development lifecycle and the security management of the business. Vulnerability Scanners and Dynamic Application Security scanners will only grab the low-hanging fruit.
Common findings often involve assets or code that have been forgotten or assumed decommissioned, leaving them out of vulnerability management programs. However, only a penetration testing team can identify misconfigurations and chain vulnerability exploits together.
An example of this would be an FTP service with a default password or easily guessable password, which could lead to malicious file upload that can be elevated to remote code execution and then reverse shell giving access remote access to the attacker. A vulnerability scanner may catch the default password but can’t chain the rest of the attack.
Adversarial Offensive Security
Adversarial Penetration Testing mimics the real threat environment as closely as possible. The offensive security exercise acts as a real-world, and most of the employees in the organization do not know the exercise is happening. This ensures it is as close to a realistic attack scenario as possible. This is not only a test of the organization’s security maturity but also provides insight into what the true risk of a successful attack would be.
Where a traditional penetration test focuses on one section of the technology infrastructure, these exercises combine all technology vulnerabilities at once. The organization then learns how the external vulnerabilities could be combined with the web application vulnerabilities to gain access.
The attack chain could include phishing, physical access, dropping Command and Control, or a simulation Ransomware. Adversarial penetration testing also allows for the combination of exploit chains from all the organization’s infrastructure. This means that a finding from a web application can be paired with phishing and then Command and Control or Ransomware. Combining vulnerabilities and exploits from all technologies provides a clearer view of the risks of these exploitations.
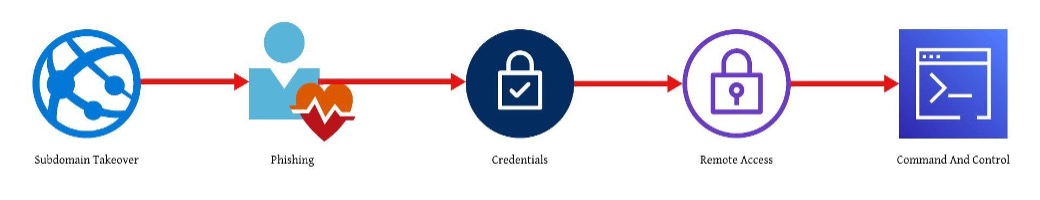
Subdomain Takeover – Phishing – Credentials – Remote Access – Command and Control
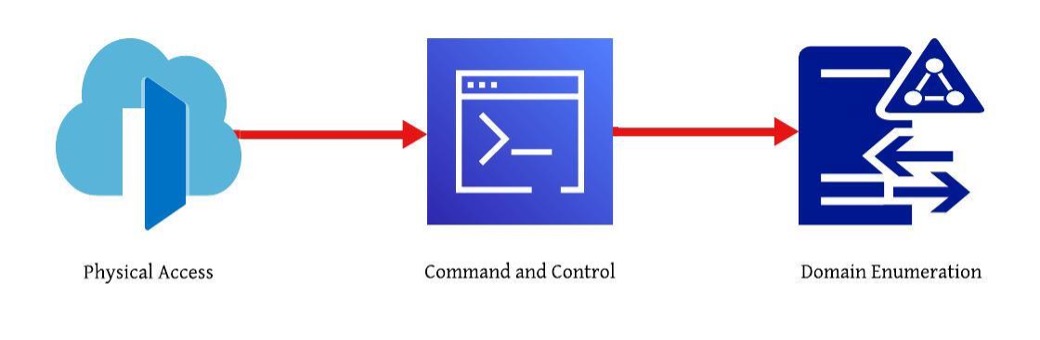
Physical Access – Command and Control – Domain Enumeration
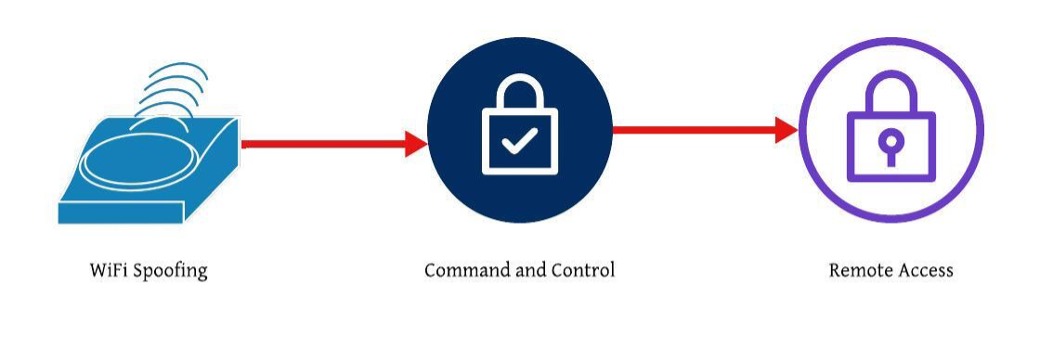
Wi-fi Spoofing – Credential Harvesting – Remote Access
The emulation of a real threat will assess the maturity of the security programs but also provide the extent of real-world attack.
- Breached Data
- Ransomware
- PII data
- Financial Data
- Account Takeover
- Cloud Keys
Adversarial Penetration Testing allows the freedom to incorporate various tactics and techniques. It is a broader process that involves potential adversarial behaviours during an attack on an organization’s systems.
- Validate an organization’s security stack and help identify gaps that may exist so that future technology investments can be based on more quantitative data points
- Improve cyber resilience following a cyber breach event
- Validate the effectiveness of security programs, tools and specific controls against industry-specific attacker techniques
Breached Data
IBM’s Breached Data report estimates that the averages 4.8 million dollars a year
https://www.ibm.com/reports/data-breach
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.





















