In today’s digital landscape, cybersecurity risk management has evolved from being a technical concern to becoming a critical business issue that directly impacts an organization’s financial stability. As organizations mature in their cybersecurity practices, the conversation shifts from simply protecting networks and systems to aligning these efforts with broader business objectives—namely, protecting the bottom line. At the highest level of cybersecurity program maturity, risk management is not just about safeguarding data and systems; it’s about understanding, quantifying, and mitigating risks in a way that resonates with boards of directors and executive leadership teams (ELTs).
Why Cybersecurity is a Business Issue, Not a Technology Concern
In the early days of cybersecurity, the focus was squarely on protecting technical assets. Firewalls, antivirus software, and patch management were the primary tools in the cybersecurity toolkit – network, identity & access management, and host protection being those three, critical technical pillars of cyber security. But as businesses have become more digitized and dependent on technology, the nature of cybersecurity threats has changed. Cyberattacks today can disrupt operations, cause reputational damage, and lead to significant financial losses.
A single data breach can cost millions of dollars, considering factors such as legal fees, regulatory fines, lost business, and customer remediation efforts. For example, IBM’s “Cost of a Data Breach” report consistently finds that the average cost of a data breach is rising, with many breaches leading to losses that exceed $4 million. This makes cybersecurity an essential consideration for boards and ELTs, whose primary concern is safeguarding shareholder value and ensuring business continuity.
This shift has necessitated a broader, more strategic view of cybersecurity that is quantifiable to dollars. At its most mature, a cybersecurity program must provide visibility into the financial risks posed by cyber threats. Only then can an organization fully protect itself, its customers, and its stakeholders.
From Technical Metrics to Business Language: Translating Cybersecurity Risks into Dollars
For cybersecurity programs to resonate with senior leadership and the board, they must move beyond technical jargon and into the realm of business language. Executives are not typically interested in the number of blocked malware infections or the uptime of firewalls. Instead, they care about how much these issues could cost the company, what measures can be taken to mitigate those costs, and how CISO’s and security leaders can strategically shape programs.
This is where cybersecurity risk management shines at its highest level of maturity. It allows cybersecurity professionals to translate vulnerabilities, threats, and risks into potential financial losses. This involves quantifying the cost of cyber incidents—such as data breaches, ransomware attacks, and system outages—in terms that the business can understand, including:
- Lost revenue due to operational disruptions or compromised customer trust.
- Regulatory fines and penalties for non-compliance with data protection laws such as GDPR or CCPA.
- Legal fees from lawsuits or settlements.
- Remediation costs for fixing the problem and compensating affected customers.
- Reputational damage that may lead to lost customers and diminished brand value.
Quantifying these costs allows the organization to assess the potential financial impact of each risk and prioritize its cybersecurity efforts accordingly. With this data, boards and ELTs can make informed decisions about which risks mitigating, transfer (through insurance), or accept based on the potential financial repercussions.
The Role of Continuous Threat Exposure Management (CTEM) in High Maturity Programs
As organizations strive for cybersecurity maturity, Continuous Threat Exposure Management (CTEM) becomes a critical component in helping them maintain a real-time understanding of their risk landscape. CTEM tools like CyberCAST enable businesses to assess their cybersecurity posture continuously, providing real-time data on vulnerabilities, threat exposure, and potential impacts.
CyberCAST, for instance, not only measures an organization’s cybersecurity maturity but also helps translate technical vulnerabilities into measurable business risks. By continuously monitoring the threat environment and simulating potential attacks, CTEM tools allow businesses to stay ahead of emerging risks. This proactive approach is essential in preventing the types of incidents that can lead to significant financial losses.
Aligning Cybersecurity with Business Objectives
At the highest level of maturity, cybersecurity becomes fully integrated with the organization’s broader risk management and business strategies. This integration ensures that cybersecurity efforts are aligned with the organization’s objectives and that resources are allocated based on the business’s priorities.
One way to achieve this alignment is through risk-based decision-making. Instead of making cybersecurity investments based on the latest trends or compliance requirements, organizations should prioritize their investments based on the risks that pose the greatest financial threat. For example, if a company’s most valuable asset is customer data, protecting that data should be a top priority, even if it requires a significant investment in security technologies or personnel.
This approach helps ensure that cybersecurity efforts contribute to the organization’s overall success by focusing on protecting its most critical assets. It also allows the board and ELTs to see the direct link between cybersecurity investments and the protection of the company’s bottom line.
Effective Communication with Boards and ELTs
Communicating cybersecurity risks to boards and ELTs can be challenging, especially when dealing with individuals who may not have a technical background. However, at the highest level of program maturity, cybersecurity leaders must be adept at communicating the business impact of cyber risks clearly and concisely.
Here are a few strategies to ensure effective communication:
- Use business language: Avoid technical jargon and instead focus on the potential financial and operational impacts of cyber risks.
- Provide context: Explain why certain risks are more critical than others by tying them to the organization’s business goals or regulatory obligations.
- Quantify the impact: Use data to quantify the potential financial loss of a cyber incident and how mitigation efforts can reduce that loss.
- Demonstrate ROI: Show how cybersecurity investments contribute to the company’s bottom line by preventing losses, ensuring compliance, or improving operational efficiency.
- Regular reporting: Provide regular updates on the organization’s cybersecurity posture and progress in mitigating risks, using metrics that matter to the business.
By framing cybersecurity risks in terms of dollars and business outcomes, boards and ELTs are more likely to prioritize and support cybersecurity initiatives.
The Bottom Line: Cybersecurity is a Business Imperative
As businesses become more dependent on digital technologies, the financial risks associated with cyber threats continue to grow. Cybersecurity can no longer be seen as just an IT issue—it is a core business issue that directly affects an organization’s financial health. At the highest level of cybersecurity maturity, risk management is not just about preventing cyberattacks; it’s about understanding how those attacks could impact the bottom line and taking proactive steps to mitigate those risks.
By adopting a mature cybersecurity risk management approach, leveraging CTEM tools like CyberCAST, and communicating risks in business terms, organizations can align their cybersecurity efforts with their broader business objectives. This not only protects the organization from financial loss but also ensures that cybersecurity investments deliver measurable value to the business. Ultimately, a mature cybersecurity program is one that successfully translates technical risks into financial realities, enabling boards and ELTs to make informed decisions that protect both the company’s assets and its future.
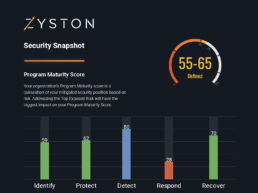
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.



















