In today’s digital age, cybersecurity is a top priority for businesses of all sizes. As cyber threats evolve, businesses increasingly turn to penetration testing. This strategy helps them identify and address vulnerabilities in their security systems before malicious actors can exploit them.
Penetration testing, also known as pen testing, is a simulated cyberattack that identifies and exploits vulnerabilities in an organization’s IT infrastructure. Pen testers use the same techniques and tools as real hackers to find weaknesses in systems and applications. This allows them to assist organizations in improving their security posture and reduce their data breach risk.
In this blog, we will discuss the primary goal of penetration testing, why it is essential, and the result of a successful test.
Why Is Penetration Testing Important?
 Pen tests offer businesses actionable insights and recommendations to enhance their cybersecurity posture. Penetration testers produce comprehensive reports detailing identified vulnerabilities, the methods used to exploit them, and remediation steps to address weaknesses effectively.
Pen tests offer businesses actionable insights and recommendations to enhance their cybersecurity posture. Penetration testers produce comprehensive reports detailing identified vulnerabilities, the methods used to exploit them, and remediation steps to address weaknesses effectively.
Additionally, proactive penetration testing offers various benefits for organizations, making it an indispensable part of a comprehensive cybersecurity strategy. Here’s a closer look at the key advantages of penetration testing:
1. Identifying Vulnerabilities
One of the primary goals of penetration testing is to identify vulnerabilities within an organization’s IT infrastructure. By employing ethical hackers to simulate attacks, businesses can uncover vulnerabilities not easily identified through traditional security assessments. This proactive approach allows businesses to address vulnerabilities before malicious actors capitalize on them.
2. Mitigating Risks
Penetration testing goes beyond merely vulnerability scanning; it plays a pivotal role in mitigating risks. By understanding potential points of exploitation, organizations can implement targeted security measures to fortify their defenses. This proactive risk management approach is essential in today’s dynamic threat landscape, where new vulnerabilities emerge regularly.
3. Ensuring Compliance
For many industries, compliance with regulatory standards is non-negotiable. Penetration testing assists businesses in meeting these standards by identifying and rectifying security gaps. Whether PCI DSS, HIPAA, or other regulatory requirements, penetration testing ensures that an organization’s security measures align with industry-specific standards.
 4. Safeguarding Reputation
4. Safeguarding Reputation
A security breach jeopardizes sensitive data and tarnishes an organization’s reputation. Penetration testing helps safeguard against reputational damage by proactively identifying and resolving security issues. Regular testing can enhance customer trust and confidence by demonstrating a commitment to cybersecurity.
5. Continuous Improvement
Cyber threats are dynamic and constantly evolving. The primary goal of penetration testing is not a one-time fix but an ongoing commitment to continuous improvement. Regular testing allows businesses to adapt security measures to emerging threats, ensuring their defenses remain resilient.
6. Cost-Effectiveness
While penetration testing may involve an upfront cost, it can significantly reduce the potential financial losses associated with cyberattacks. By preventing breaches, businesses can save themselves from costly expenses related to data recovery, downtime, and reputational damage. Overall, penetration testing is cost-effective for enhancing an organization’s cybersecurity posture.
Best Practices for Penetration Testing
 To maximize the effectiveness of penetration testing, organizations should adhere to best practices, which include:
To maximize the effectiveness of penetration testing, organizations should adhere to best practices, which include:
1. Comprehensive Scope Definition
The effectiveness of penetration testing hinges on a well-defined scope. Businesses should work with their cybersecurity service provider to clearly outline the systems, networks, and applications to be tested. A comprehensive scope examines all critical areas, providing a holistic view of an organization’s security.
2. Realistic Simulation
Penetration testing must simulate real-world attack scenarios to achieve meaningful results. Ethical hacking should involve tactics, techniques, and procedures (TTPs) commonly used by malicious actors. Realistic simulations enable businesses to identify how well their security controls can withstand genuine threats.
3. Engaging Experienced Professionals
Engage the services of experienced and certified penetration testing professionals. Collaborating with experts ensures that the testing is conducted with the highest standards of expertise and ethical considerations. Find a security service provider with a proven track record in delivering reliable and effective penetration testing services.
 4. Collaboration with Internal Teams
4. Collaboration with Internal Teams
Successful penetration testing requires collaboration between external cybersecurity experts and internal IT teams. Internal stakeholders possess valuable knowledge about the organization’s computer systems and processes, aiding ethical hackers in their assessments. This collaboration ensures a more accurate representation of an organization’s security landscape.
5. Prioritize Remediation
Identifying potential vulnerabilities is only half the battle; timely remediation is equally crucial. A structured and swift process of addressing and patching vulnerabilities should follow a pen test. This proactive approach minimizes the window of opportunity for potential attackers.
6. Regular Testing Cadence
The threat landscape is dynamic, with new security vulnerabilities emerging regularly. As such, penetration testing should not be a sporadic activity but a regular and recurring process. Establishing a testing cadence ensures that an organization’s security measures remain effective against evolving threats.
Elevate Your Security Defenses with Zyston
Penetration testing is an important part of any organization’s cybersecurity strategy. Businesses can reduce the risk of breaches and other security incidents by identifying and addressing system vulnerabilities. By continuously improving and following best practices, penetration testing helps organizations stay ahead of threats and protect their assets.
As a full-service managed security service provider, Zyston understands the critical role that penetration testing plays. That’s why we provide innovative, reliable, supportive, and strategic penetration testing services designed to empower businesses to thrive.
Partner with Zyston to experience proactive and comprehensive penetration testing services that strengthen your security posture. Contact us today to learn more about how we can protect your business from cyber threats.
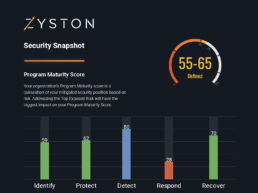
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.



















