Penetration testing, often referred to as pen testing, is a crucial component of any organization’s cybersecurity strategy. It’s a proactive approach that allows identifying and addressing vulnerabilities in your digital infrastructure before cybercriminals can exploit them.
In this blog, we will delve into the world of penetration testing. We will explain what it is, its scope, the process involved, and why it’s an essential practice in today’s threat landscape.
What Is Penetration Testing?
 Penetration testing is a controlled and simulated cyberattack on an organization’s digital assets to identify vulnerabilities and weaknesses that malicious actors could exploit. It involves using various techniques and tools to assess the security posture of an organization’s IT infrastructure. This consists of analyzing computer systems, networks, applications, and other components.
Penetration testing is a controlled and simulated cyberattack on an organization’s digital assets to identify vulnerabilities and weaknesses that malicious actors could exploit. It involves using various techniques and tools to assess the security posture of an organization’s IT infrastructure. This consists of analyzing computer systems, networks, applications, and other components.
At Zyston, we offer full-service pen testing solutions. Using our proprietary platform, CyberCAST, we identify and intentionally exploit vulnerabilities to gain insight into the most effective mitigation strategies. With the insights we gather, we develop a customized plan that meets your specific needs and addresses the wider concerns of your industry.
The end goal of penetration testing is to provide organizations with actionable insights into their security vulnerabilities. It also recommends remediation measures to improve their overall security posture. Certified pen testers with expertise in cybersecurity perform the simulated attacks. They are often referred to as “ethical hackers” or “white-hat hackers.”
The cost of penetration testing can vary based on the complexity of your network and the depth of testing. However, it is important to view this as an investment in your organization’s security rather than an expense. Additionally, the cost of a pen test is typically much lower than that of a security breach.
What Is the Scope of a Penetration Test?
 The scope of a penetration test can vary depending on your organization’s specific needs and objectives. Here are the key areas typically covered in a penetration test, each discussed in detail below:
The scope of a penetration test can vary depending on your organization’s specific needs and objectives. Here are the key areas typically covered in a penetration test, each discussed in detail below:
Network Penetration Testing
This phase identifies exploitable vulnerabilities in your network infrastructure, including routers, switches, firewalls, and other devices. It assesses the potential points of entry for an attacker and checks for misconfigurations or weak network security settings.
Application Penetration Testing
Application security is vital in today’s digital landscape. Penetration testers examine web applications, mobile apps, and other software for weaknesses. This often involves identifying vulnerabilities like injection flaws, authentication issues, and authorization problems.
Wireless Network Testing
With the increasing use of wireless networks, it’s essential to ensure they are secure. This phase involves testing for weaknesses in Wi-Fi networks, including encryption protocols, access points, and potential weak spots.
 Cloud Infrastructure Testing
Cloud Infrastructure Testing
As more organizations move to the cloud, it’s critical to ensure their cloud infrastructure is secure. Penetration testing can help identify misconfigurations or weak access controls in your cloud environments.
Social Engineering Testing
One of the most common attack vectors is social engineering, where attackers manipulate individuals to gain access to systems. Penetration testing teams may conduct phishing simulations or physical security tests to evaluate an organization’s susceptibility to social engineering attacks.
Physical Security Testing
Physical access to an organization’s premises or devices can also pose a significant security risk. Pen testers may try to physically access restricted areas, like server rooms or data centers, to assess vulnerabilities.
Database Testing
Databases contain valuable data, making them a prime target for attackers. Testers assess the security of your databases, looking for vulnerabilities that could lead to data breaches. This may include SQL injection attacks, weak authentication methods, and unencrypted data.
The Penetration Testing Process
 The penetration testing process typically follows a well-defined set of steps, providing structure and consistency to the evaluation. These steps include:
The penetration testing process typically follows a well-defined set of steps, providing structure and consistency to the evaluation. These steps include:
1. Planning
The first phase involves understanding the organization’s objectives and defining the scope of the penetration test. This step ensures that the test aligns with your specific security goals. It also involves gathering information about the organization’s systems, networks, and applications to understand potential attack vectors.
2. Scanning and Reconaissance
Once the scope is defined, the testers perform reconnaissance to identify potential vulnerabilities. They may use automated tools or manual techniques to scan for open ports and services. They try to find any information that could aid in accessing your systems.
3. Exploitation
Next, the testers attempt to exploit the identified vulnerabilities to gain access to your systems. This step involves using various techniques and tools, such as password cracking and SQL injection, to penetrate your defenses.
4. Post-Exploitation
After gaining access, the testers assess whether they can escalate privileges or move laterally within the network. They may also attempt to cover their tracks to evade detection.
5. Reporting
The final phase involves compiling a comprehensive report that outlines the vulnerabilities, their severity, and recommended remediation measures. This report provides valuable insights for improving security posture and mitigating potential risks. The work doesn’t end with the report. It’s crucial to address the identified vulnerabilities, strengthen security, and prevent potential breaches.
It’s also important to note that penetration testing is not a one-time event but rather an ongoing process. The frequency of penetration testing varies from one organization to another. However, it is generally advisable to conduct regular tests to stay ahead of evolving threats. Annual testing is common, but high-security organizations or those in high-risk industries may require more frequent testing.
Strengthen Your Defenses with Penetration Testing
Penetration testing is a crucial step in safeguarding your organization’s valuable data and assets. It helps identify vulnerabilities before attackers can exploit them, allowing you to address them proactively. By regularly conducting penetration tests, you can strengthen your defenses and minimize the risk of security breaches.
At Zyston, we specialize in penetration testing services designed to meet your unique security needs. Our team of ethical hackers is ready to assist you in identifying and addressing vulnerabilities within your digital infrastructure. Don’t wait for a breach; contact Zyston now to learn more about our penetration testing services and take proactive steps to secure your organization.
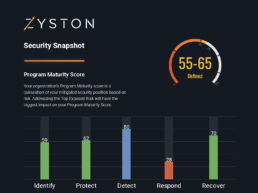
CyberCast Security Reporting
Security reporting that speaks business
Zyston CyberCAST brings the world of cybersecurity metrics up out of the weeds and into the hands of executive decision makers so nothing gets lost in translation. With CyberCAST, your organization gets clear visibility on security risks and also how your organization scores against your industry peers.




















